Abstract: Industrial Ethernet, as a new direction in the development of control system networking, has also gradually penetrated into industrial control networks. Therefore, the coexistence of standard and diversified fieldbuses and industrial Ethernet will exist for a long time. This article conducts an in-depth study on the interconnection communication mechanism between heterogeneous networks, and analyzes some problems existing in each mechanism, such as high development costs, poor scalability and portability. Based on a detailed analysis of the working mechanism of the protocol conversion gateway, a protocol conversion gateway based on the embedded middleware protocol library is proposed. Utilize layered ideas and software reuse technology to design the scalability and portability of the protocol library; hierarchize and componentize the protocol library, and define the principles and granularity control of the componentization of the embedded middleware protocol library; and use Shared memory technology realizes the exchange of data information. Finally, an easily portable and scalable embedded protocol conversion gateway is designed and developed to realize interconnected communication between multiple protocols.Keywords: Fieldbus protocol conversion protocol library
Abstract: Industrial Ethernet, as a new direction of network development of control systems,has gradually penetrated in o industrial control networks, so the standard The coexistenceof quasi-diversified fieldbus and industrial Ethernet will exist for a long time. In this paper,the interconnection communication mechanism between heterogeneous networks is deeplystudied, and some problems existing in each mechanism, such as high development cost, scalability and poor portability, are analyzed. Based on the detailed analysis of the workingmechanism of the protocol conversion gateway, a protocol conversion gateway based on the embedded middleware protocol library is proposed. The layered idea and softwarereuse technology are used to design the scalability and portability of the protocol library. The protocol library is hierarchical and componentized, and the principle and granularity control of the component library of the embedded middleware protocol library are defined . Sharedmemory technology enables the exchange of data information. Finally, the design and implementation of a portable, scalable embedded protocol conversion gateway based on multi-protocol interconnection communication. Key words: Fieldbus Protocol conversion Protocol library.
1 Introduction:
In the field of automation control, fieldbus has been widely used in the underlying control network. However, with the development and technological changes of network technology and embedded technology, the demand for intelligence is growing day by day, and the networking and openness of control systems have become the development trend of the industry. trend. At present, fieldbus technology itself still has certain limitations. In particular, the existing several international standard fieldbuses are incompatible and competitive with each other in terms of communication protocols and bus standards, and cannot achieve interoperability. This seriously limits the fieldbus Developments in the field of control. In the process of upgrading and transforming the control network system, because different on-site embedded device manufacturers adopt different communication methods and there is no universal software protocol between them, the communication used to connect embedded devices in the industrial intelligent network Hardware media vary widely, as do fieldbuses and communication protocols, forming an incompatible heterogeneous network that lacks openness and compatibility.
2 Introduction to network communication related technologies
PLC has some characteristics of a general-purpose computer, but its working method is very different from that of a general-purpose computer. It adopts a cyclic scanning working method. The principle can be explained as the task program is processed according to a certain access sequence and execution sequence. Every time a scan cycle is completed, the user program is executed in a loop from the beginning, and the operation is repeated. Its working process is shown in the figure, which mainly includes three stages: input sampling stage, program execution stage, and output scanning stage.
As shown in Figure 1, it mainly includes three stages: input sampling stage, program execution stage, and output scanning stage.
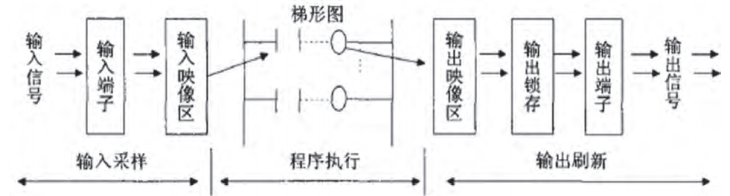
Figure 1 PLC working principle diagram
As communication protocols become a critical component of an embedded control network, the need for new protocols that meet high bandwidth and predictability requirements increases. There are a variety of real-time communication protocols. Among these protocols, the protocols that can meet vehicle reuse include: Controller Area Network (CAN), Local Internet Network (LIN) and SAE J1850 are currently in large-scale use. In addition, only a few protocols are suitable for security applications with mandatory requirements of predictability. A survey and comparison of communication protocols for embedded systems that meet security requirements in the literature shows that data communication activities must be able to be triggered, whether it is a dynamic response based on events, Or static triggering based on time polling [3]. On the one hand, there are static scheduling information protocols based on time processing, such as the SAFE BUS and SPIDER protocols used in the avionics industry, TTCAN and the time-triggered protocol TTP used in the automotive industry. On the other hand, some are communication protocols that dynamically schedule information. For example, Controller Area Network (CAN) is widely used in various fields, and LONWORKS protocol and PROFIBUS protocol are commonly used in real-time systems. Among them, CAN bus is the most well-known and widely used event-driven communication protocol in the field of distributed embedded real-time systems.
3. Research on congestion control algorithm in embedded gateway
3.1 Active Queue Management Policy Control Model In order to solve the problem that data communication activities must be triggered deterministically, proactive rather than responsive packet discarding is an effective means. The corresponding queue management strategy is called active queue management, which is the mainstream algorithm for buffer queue management. The basic idea is that according to the change of the queue length, before the queue buffer overflows, the arriving packet data is discarded with probability. The discard mark signal of the packet is detected by the source end after a delay, and the source end determines the network status based on this. State, the corresponding control algorithm is called according to different states to adjust the sending rate, so that the queue length in the router cache is controlled.In this way, the strategy forms a closed-loop control system, in which is the controller, whose output is the control signal of the system, and the rate control algorithm at the source end is the executor of the system, which together with the queue length characteristics of the router and the link delay, Generalized objects that make up the system, as shown in Figure 2
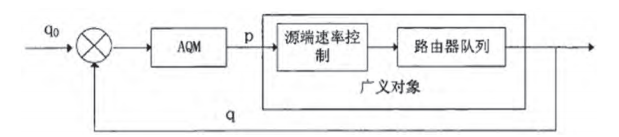
Figure 2 Active queue management policy control model
Research on link algorithms is currently focused on the “Active Queue Management” (Active Queue Management, AQM) algorithm. Compared with the traditional “Droptail” (Droptail), AQM discards or marks messages before the buffer overflows of the network device. .
3.2 Main advantages of AQM
(1) Reduce packet loss at the gateway. Using AQM can keep the queue length small, thereby enhancing the ability of network intermediate nodes to accommodate burst traffic [6].
(2) Reduce the delay of packets passing through the gateway. Reducing the average queue length can effectively reduce the queuing delay of packets in network devices.
(3) Avoid the occurrence of Lock-out behavior.
3.3 RED algorithm
A representative algorithm of AQM is the RED (random early detection) algorithm. RED has better performance than Droptail. In RFC2309, RED is strongly recommended as the future standard. However, further research found that the performance of RED is very sensitive to the parameter settings of the algorithm, and it has not been widely used in the Internet so far. According to the results provided in the literature, RED performs better than Droptail, but it has two main flaws:
(1) RED is very sensitive to parameter settings, and changing parameters has a great impact on performance. So far, there is no clear method for determining these parameters;
(2) As the number of “flows” in the network increases, the average queue length of the gateway will gradually increase, which is also detrimental to improving real-time performance.
4 Protocol conversion gateway design
4.1 Gateway composition structure The protocol conversion gateway mainly includes the core processor, Ethernet controller, RS485/232 transceiver and other field bus controllers, peripheral I/O equipment, off-chip memory, etc. The gateway composition structure is shown in Figure 3.
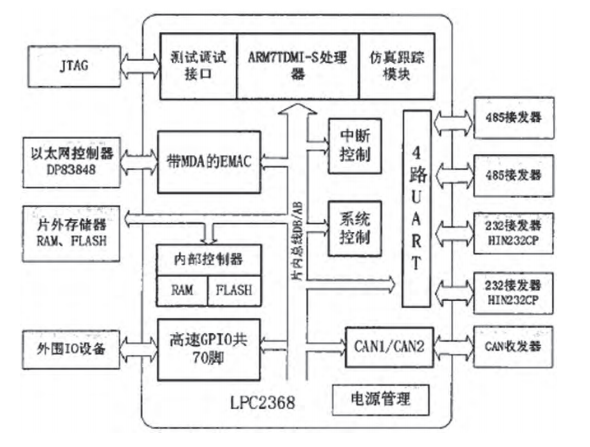
Figure 3 Gateway hardware structure diagram
(1) The request and control information data reaches the gateway through the Ethernet link, and the Ethernet control chip in the gateway realizes the data flow of the Ethernet physical layer; (2) The EMAC module of the processor processes the data and obtains the link Valid data of the layer;
(2) The EMAC module of the processor deconstructs the data and obtains valid data at the link layer;
(3) These data are handed over to the gateway conversion program for processing through the high-speed bus (AHB) to obtain the original request and control information;
(4) Then encapsulate the data according to the target bus protocol format, and select the corresponding bus channel in the chip to send the data;
(5) The data frame reaches the corresponding physical bus link through the off-chip bus transceiver module connected with these bus channels. The reverse conversion is the reverse circulation of the above data process to realize data forwarding across the network.
4.2 Software hierarchy diagram
In the system program structure design, the embedded communication middleware software design idea is introduced. Each device is abstracted, and the implementation of the network protocol library adopts a hierarchical structure design, using information mechanisms to achieve access between layers, shielding the access details of the upper layer to the lower layer, realizing transparent calling of program interfaces, and facilitating cross-platform transplantation and debugging of programs. [8]. The software hierarchy is shown in Figure 4.
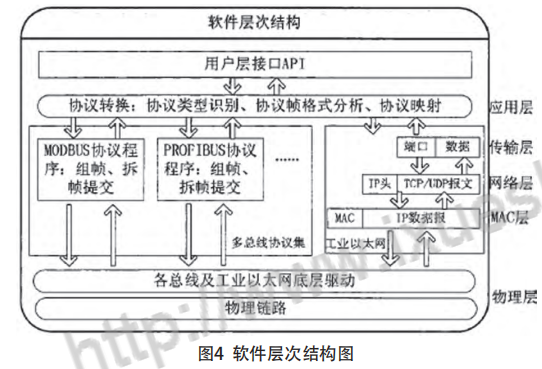
Summarize:
The heterogeneous hardware architecture and heterogeneous communication protocols in the control network are analyzed, focusing on various bus network communication protocols and communication characteristics. Research and analysis of interconnection communication mechanisms between heterogeneous networks, propose and complete the design of a protocol conversion gateway based on the embedded middleware protocol library, define the principles and granularity control of the componentization of the embedded middleware protocol library, and use shared memory technology to achieve Data exchange. Complete the software and hardware design and implementation of the protocol conversion gateway, including the design and implementation of the protocol library, the design of the unified access interface, and the implementation of the conversion process. In order to ensure the service quality of the protocol conversion gateway in the heterogeneous control network link, in view of the complex uncertainty factors in the communication protocol conversion process, the advantages and disadvantages of the information network congestion control technology, source-side congestion control algorithm and link control algorithm are analyzed. A congestion control strategy based on fuzzy control is proposed.
Disclaimer: This article is reproduced online. If it is harmful to your interests, please contact us to delete it.
