The international standardization organizations IEEE and IETF are working together to develop a highly reliable, low-power wireless communication protocol stack for the Internet of Things that can access the Internet. IEEE is mainly responsible for formulating standards for the physical layer and link layer of Internet of Things communication protocols, such as the IEEE802.15.4-2006 standard, of which IEEE802.15.4e is the latest link layer standard. The IETF is mainly responsible for formulating the network layer and above standards for Internet of Things communication protocols, such as 6LoWPAN, RPL and CoAP standards, which can connect resource-limited sensor nodes to the Internet. Network security is the basis for the large-scale development of the Internet of Things. A safe and efficient mechanism must be designed to ensure the normal operation of communication protocols. This article introduces the Internet of Things communication protocol stack in detail, focusing on analyzing and discussing the latest research progress in its security. Finally, the research direction of secure communication protocols for the Internet of Things is summarized and prospected.
The International Telecommunications Union (ITU) released a report on the theme of “Internet of Things” in 2005. The report proposed for the first time that “the Internet of Things will use barcodes, radio frequency identification and sensors and other sensing devices to achieve the goal through a set of standard communication protocols.” Intelligent identification and real-time status monitoring of any item” [1-3]. At present, a new round of industrial revolution has launched in major developed countries around the world, and countries are beginning to apply new technologies such as the Internet of Things and big data to the industrial intelligent manufacturing process [4-5]. The United States first proposed the concept of “Industrial Internet of Things” in 2012, applying new Internet of Things technologies to high-end manufacturing to achieve the purpose of revitalizing advanced manufacturing in the United States. Germany proposed the “Industry 4.0” strategic plan in 2013, which aims to upgrade traditional manufacturing factories to smart factories by building cyber-physical systems to connect various elements such as products, equipment and people. In 2015, my country released the “Made in China 2025” strategic plan, which pointed out the task of “promoting the deep integration of new generation information technologies such as the Internet of Things and big data with traditional manufacturing, and promoting the transformation and upgrading of traditional manufacturing to intelligent manufacturing.” It can be seen that applying new technologies of the Internet of Things to future industrial applications is an inevitable development trend.
Currently, the International Organization for Standardization IEEE and IETF are working together to develop a set of highly reliable, low-power wireless communication protocols that can be connected to the Internet for the Industrial Internet of Things. Data in the industrial manufacturing process (such as rotation speed, vibration, temperature, humidity, acceleration, etc.) are collected in real time through a large number of cheap, resource-limited sensor nodes, and then a set of standard wireless communication protocols are used for single-hop or multi-hop transmission. Finally, the collected data is sent to the remote server through the border router. The IEEE working group is mainly responsible for formulating standards below the link layer, such as the IEEE802.15.4-2006 standard [6], of which IEEE802.15.4e[7] is the latest version of the link layer standard. The IETF working group is mainly responsible for formulating standards above the link layer, including adaptation layer 6LoWPAN [8], network layer IPv6RPL [9] and application layer CoAP [10] standards, which can implement resource-constrained sensor nodes and next-generation IPv 6Internet for interconnection.
Since the Internet of Things is widely used in national infrastructure fields such as petroleum, petrochemicals, coal mines, and power grids, the security issue of the Internet of Things will be a key issue that must be solved during its development and application. The Stuxnet virus in 2010 caused multiple industrial control networks around the world to fail to work properly (such as the Iranian nuclear power plant accident). In 2015, hackers launched a malicious code Black Energy (black energy) attack on Ukraine’s power system, resulting in serious consequences such as long-term and large-scale power outages. In the Mirai incident in 2016, attackers used hundreds of thousands of IoT devices such as web cameras to launch DDoS attacks on domain name servers, causing a large number of users to be unable to use network services normally. In addition, the seven deadly attacks released by RSA2017, the most influential industry event in the information security community, include attacks on the Industrial Internet of Things. It can be seen that attacks on the Internet of Things are currently emerging in endlessly, and they are increasingly valued by the government and academia.
However, there are still many serious security issues in current IoT communication protocols. Literature [11-14] pointed out that there are security vulnerabilities in the link layer of the Internet of Things protocol stack, and attackers can launch time synchronization attacks, tampering attacks, and energy exhaustion attacks. Literature [15-17] pointed out that there are various security vulnerabilities in the RPL protocol in the IoT protocol stack. Attackers can launch witch attacks, selected forward attacks, HELLO flooding attacks, and wormhole attacks, etc., thereby destroying the normal operation of the RPL protocol. This article first introduces the IoT protocol stack and its security architecture; then discusses the latest research progress in the security standards and mechanisms of the physical layer and link layer, 6LoWPAN adaptive layer, RPL routing layer and CoAP application layer in the IoT communication protocol stack; Finally, the research direction of secure communication protocols for the Internet of Things is summarized and prospected.
1 Internet of Things protocol stack and its security architecture
1.1 Internet of Things Communication Protocol Stack The work goal of the international standardization organizations IEEE and IETF is to design a highly reliable, low-power, Internet-accessible communication protocol stack on resource-constrained sensor nodes so that it can support Hundreds or thousands of nodes perform self-organized multi-hop communication. The IEEE working group published the IEEE802.15.4-2006 standard [6] in 2006, which is suitable for short-distance and low-power consumption scenarios. The physical layer of this standard stipulates that the maximum data transmission rate is 250kbps and operates in the ISM frequency band, in which 2 There are 16 channels in the 4GHz frequency band. In addition, the IEEE802.15.4-2006 standard uses optional time slots to guarantee the GTS mechanism and CSMA-CA channel access mechanism, and supports the ACK mechanism to ensure reliable transmission. So far, this standard has become the physical layer and standard of protocols such as Zig-Bee [18], WirelessHART [19], ISA100.11a [20] and WIA-PA [21]. Link layer basics. However, wireless communications based on the IEEE802.15.4-2006 standard have exposed many problems in terms of low power consumption and reliability. In 2008, DUST proposed a TSMP (Time-Synchro) nizedMeshProtocol) time synchronization technology [22]. TSMP uses time division multiple access TD-MA technology to avoid idle monitoring of nodes in the network, reducing network energy consumption. It also uses time slot frequency hopping mechanism to solve the problems of multipath attenuation and external network interference, and improves the reliability of wireless transmission. In 2012, the IEEE802.15.4 working group officially released the IEEE802.15.4e standard. Its core technology is TimeSynchronization Channel Hopping (TimeSynchronization Channel Hopping). ionChannelHopping, TSCH), among which TSMP technology is the basis of TSCH. In the IEEE802.15.4e network, nodes turn on or off radio frequencies at predetermined times through precise time synchronization, thereby saving node energy consumption; in addition, nodes adopt a time slot-based frequency hopping mechanism, thereby enhancing the node’s resistance to surrounding Robustness against environmental noise interference and multipath interference [23].
The IETF working group is mainly responsible for the formulation of high-level standards such as the application layer, network layer and adaptation layer of the protocol stack. IETF has successively established three working groups, namely 6LoWPAN (IPv6overLowpower) ersonalArreaNetworks) Working Group, ROLL (Routing GoverLossia ndLow-po-werNetworks) working group and CoRE (ConstraineedRestful Environ-ment) working group. The IETF6LoWPAN working group is responsible for developing IPv6 protocols that can run on low-power personal area networks. The IETFROLL working group is responsible for developing the IPv6RPL routing protocol that can run on low-power and lossy networks [9]. The IETFCoRE working group is responsible for developing a lightweight application layer CoAP protocol [10] that can run on resource-constrained nodes, so that resource-constrained nodes can communicate with the existing Internet. In addition, IETF established 6TiSCH (IPv6overtheTSCHmodeofIEEEE802. 15.4e) Standards Group [24], responsible for the design of the IPv6 protocol in IEEE802.15.4eTSCH mode. The latest progress of this working group in security includes low-overhead secure network access. Mechanism and 6TiSCH security architecture design.
1.2 Security Architecture The security objectives of the Internet of Things are basically the same as those of other networks, which mainly include five objectives: confidentiality, integrity, availability, non-repudiation and data freshness. Confidentiality refers to ensuring that confidential information will not be leaked to unauthorized entities through the use of information encryption and decryption technology. Integrity refers to ensuring that information will not be tampered with by using technologies such as integrity authentication, hashing and digital signatures. Availability refers to the use of technical means such as fault tolerance, intrusion detection or network self-healing to ensure that the network can still provide normal services in the event of an attack. Non-repudiation means that the initiator of the information source cannot deny the information sent by himself. Commonly used technologies include signature, identity authentication, and access control. Data freshness refers to ensuring that users get the information they need within a specified time. Commonly used technologies include network management, intrusion detection, and access control. In addition, the security goals of IoT also include privacy, anonymity and trust.
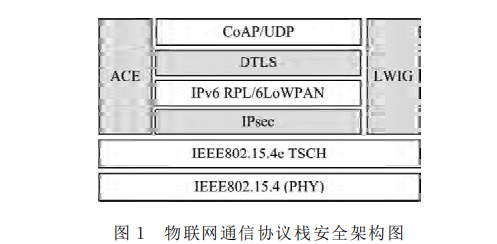
Figure 1 shows the security architecture of the IoT protocol stack. CoAP is a REST architecture IoT application layer protocol based on UDP protocol, using DTLS (DatagramTransport-Laye rSecurity) [25-26] provides end-to-end secure transmission. DTLS is an extension of the existing TLS security protocol architecture, and TLS is mainly used to ensure the security of data transmitted on TCP and cannot be used to ensure the security of data transmitted on UDP. Through extension, DTLS can support the secure transmission of UDP datagrams. The RPL protocol [9] uses IPSec to provide secure transmission at the network layer. IPSec provides security services such as network layer packet encryption, source address authentication, and access control. Authentication and Authorization in Constrained Environments (Authentication and Authorization) The Rained Environments (ACE) working group is developing an authentication authorization mechanism for access to resources hosted on servers in restricted environments, and recently completed a comprehensive use case document RFC7744 [27]. The Constrained Environments (DTLSInConstrainedEnviron-ments, DICE) working group is studying D for constrained IoT devices. TLS protocol. In addition, lightweight implementation guidance (Light-WeightImple-mentation Guidance, LWIG) work The group provides a minimal IP communication protocol stack and related security technologies for resource-constrained environments, including asymmetric encryption technology and IKEv2 authentication protocol.
2 Physical layer and link layer protocol security
The IEEE802.15 working group was established in 1998. The working group is committed to standardizing the physical layer (PHY) and link layer (MAC) of wireless personal area networks (WPAN) to provide communication standards for wireless communication devices that communicate with each other over short distances. . IEEE802.15 Task Group TG4 was established in 2000 to formulate the IEEE802.15.4 standard and develop standards for low-rate personal area networks (LR-WPAN). 2.1 Physical layer protocol – IEEE802.15.4 IEEE802.15.4 physical layer defines three frequency bands: 868MHz, 915MHz and 2.4GHz , among which 868MHz and 915MHz provide three modulation methods: BPSK, ASK and O-QPSK , 2.4GHz only provides the O-QPSK modulation method, and the data transmission rate can reach up to 250kbps. At present, the three major industrial wireless international standards WirelessHART [19], ISA100.11a [20] and WIA-PA [21] all adopt IEEE802.15 on the physical layer. 4 standards. In addition, in order to achieve global interconnection, most only use the 2.4GHz frequency band of IEEE802.15.4. 2.2 Low-power link layer protocol – IEEE802.15.4e Many industrial applications have strict requirements on the reliability, low-power consumption and real-time performance of wireless communications. The previous IEEE802.15.4-2006 standard The above requirements cannot be met. The IEEE working group began to formulate the IEEE802.15.4e[7] standard and officially released it in 2012. The core of the standard is TSCH technology. In the network, nodes turn on or off radio frequencies at predetermined times through precise time synchronization, which avoids idle monitoring of nodes and saves node energy; nodes use different channels in different time slots through time slot frequency hopping technology, which enhances their anti-interference capabilities. Improved reliability of wireless communications. Studies have shown [28-30] that even in harsh industrial wireless environments, TSCH technology can achieve a network packet loss rate of less than 0.01%. Figure 2 shows a schematic diagram of node communication in the IEEE802.15.4e network. The horizontal axis of the matrix represents the time slot value (ASN), which increases over time. A slot frame is a combination of multiple time slots that can be repeated periodically. The matrix represents the channel value vertically, and its value is between 0 and 15. There are nodes A, B, C and D in the network. Assume that the time slot-channel in the matrix is defined as [slot value, channel value]. Nodes A and B communicate at [1, 1], and nodes A and C communicate at [1, 1]. [2,4] for communication, then it can be seen that node A can use different channels for communication in different time slots.
