With the rapid development of information technology, the dependence of private information and business information transmission on wireless communication networks is significantly increasing, and the resulting attention to the security issues of the communication system itself is also rapidly increasing. As shown in Figure 1, based on the open system interconnection 7-layer protocol, the information security mechanism of the traditional communication system is established at the network layer and the layers above. Its core technology is the key encryption mechanism. The premise is that the underlying physical layer of the protocol has been Provides smooth and error-free transmission links, but physical layer information security issues have not attracted enough attention. However, due to the openness and versatility of the electromagnetic signal transmission environment, within the effective coverage of the transmit power, any third party with suitable equipment can quietly access the network to steal other people’s information, which brings serious challenges to the privacy and security of wireless communications. Comes a huge threat. With the speed of wireless data transmission, the diversification of wireless services, and the widening of wireless applications, the harm and losses caused by information theft are difficult to estimate. Therefore, compared with wired networks whose physical transmission media are relatively closed, the physical layer information security problems of wireless communication networks are more serious, and research and improvement on them are urgent.
Introduction to star networking
In a star topology, each node in the network is connected to a central node in a point-to-point manner, and the central node transmits information to the destination node. The star network topology is shown in the figure below:
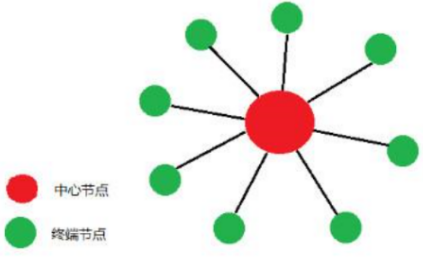
1. Any two nodes in the star network must be controlled by the central node to communicate.Therefore, the central node has three main functions:
(1) When the site that requires communication sends a communication request, the controller checks whether the central node has an idle channel and whether the called device is idle, thereby determining whether a physical connection between the two parties can be established;
(2) This channel must be maintained during the communication process between the two devices to ensure the reliability of data transmission;
(3) When communication is completed or unsuccessful and requires disconnection, the central transfer station should be able to remove the above channel.
Compared with a ring network where one node failure will cause the entire network to be paralyzed and it is difficult to locate branch node faults, a star network facilitates centralized control because the communication between terminal nodes must pass through the center. node. Due to this feature, it also brings advantages such as easy maintenance and safety. When the terminal node device is down due to failure, it will not affect the communication between other end users. The network delay time is small and the system reliability is high.
2. The main advantages of star topology are
(1) Easy to manage and maintain. Since all data communications pass through the central node, the central node can collect all communication status.
(2) Node expansion, simple structure, and easy movement. Compared with other network topologies, the star topology is easy to manage and maintain. When a node is expanded, it only needs to establish a connection with the central node device, and it will not “affect the whole situation” like a ring network.
(3) Easy to diagnose and isolate faults. Since each terminal sub-node is connected to the central node, it is easy to test each node from the central node, and it is also convenient to separate the faulty node from the system.
Because star networking has the above advantages, it has become one of the most widely used and preferred network topology designs in networking methods. However, how to avoid communication conflicts among multiple nodes in a star network has become the most important problem.
Star networking method
In the star topology, in order to effectively avoid communication conflicts between nodes, the central node and the terminal node mainly interact in the following two common ways. One is the active polling mode, and the other is the passive time slice mode. These two The introduction and comparison of networking methods are as follows:
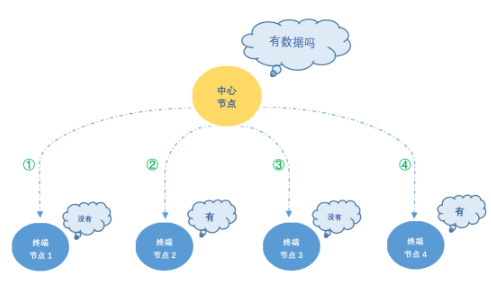
1. Active polling method
In the active polling mode, each terminal node has its own unique ID number. The central node actively asks the terminal nodes in sequence according to the ID number of the terminal node whether there is data to be sent. If a terminal node has data to send to the central node, then The central node starts processing the received data. The following figure is a schematic diagram of the active polling method:
advantage
(1) Terminal nodes are not restricted by time slices and are more free;
(2) When the interaction between the terminal node and the central node is infrequent, in theory there is no requirement for the length and time of the transmitted data;
(3) The network has high stability. The passive time slice method has higher requirements for the consistency of the crystal oscillators of each node, while the active polling method will not affect the communication of each node due to the slight deviation of the crystal oscillator ;
(4) The program structure is simpler, clearer and easier to understand than the passive time slice method;
shortcoming
(1) If a terminal node continuously sends data, it will directly affect the communication between other terminal nodes and the central node, which may cause other terminal nodes to be unable to communicate with the central node normally.
(2) Since the terminal node does not have the function of actively sending data, it must be inquired by the central node before it can send data. Therefore, the terminal node that has not been polled cannot send it immediately even if it has data .
(3) If there are more terminal nodes in the network, the more time it takes for the central node to poll the terminal nodes once, and the greater the network delay.
2. Passive time slice method
Passive time slice means that the central node will regularly synchronize the time of all terminal nodes in the network. A terminal node can only send data within its own time slice, which cannot be longer than the time allocated by the system. It is necessary to ensure that the task is executed within the time it needs to be executed. When the time comes, you can enter the task that should be executed.
advantage
(1) The communication efficiency of the passive time slice method is higher, saving the time required for central node polling in the active polling method. Since the active polling method requires the central node to query the terminal nodes in sequence according to the ID number of the terminal node during communication to ensure that the data of each node does not conflict and ensure the reliability of the network, but the query process is If there is no valid data being interacted with, the query time is “invalid” from the perspective of data transmission.
(2) The time slice of each terminal node can be set, which is more flexible;
(3) Due to the time slice mechanism, each terminal node is independent of each other, making data interaction more orderly;
shortcoming
(1) When writing a program, the time slice needs to be set reasonably, and the time for each terminal node to interact with the central node is relatively strict. Setting the time slice too short will lead to too many interrupts and task switching, reducing CPU efficiency; setting it too long may cause poor response to terminal node interaction requests;
(2) The central node must send synchronization commands regularly to avoid the time of each node being out of sync due to the deviation of the crystal oscillator between terminal nodes. If the central node does not send synchronization commands, it may lead to time slice confusion, data transmission errors or even It’s a case of network crash.
(3) The data of each terminal node can only be sent within its own time slice. If the data is not sent within the specified time slice, it can only wait until the next time to continue sending.
In general, the active polling method is suitable for situations where the real-time requirements are not high and the data transmission volume is large each time. The passive time slice method is more suitable for situations where the real-time requirements are high and the data transmission volume is small.
Other reading:
Wyner proposed the WTC-I model in 1975. In the WTC-I model, the legitimate receiver and the illegal third-party passive eavesdropper receive the data sent by the sender at the same time. As shown in Figure 2, under the assumption that the channel quality of the illegal third-party passive eavesdropper is inferior to the main channel, that is, the channels of the legitimate communicating parties must have an advantage in quality, without relying on shared keys, the transmission rate does not exceed the safe capacity . Under the premise, perfect secret communication can be achieved through reasonable security coding scheme. In addition, the physical layer keyed secure transmission technology advocated by Maurer requires generating keys based on channel characteristics. Although it can solve the problem of key distribution and management, it still needs to be combined with upper-layer encryption technology to achieve secure communication. It is a type of cross-layer secure communication. technology. [0004] ZigBee is a low-power local area network protocol based on the IEEE802.15.4 standard . ZigBee technology is a short-distance, low-power wireless communication technology. It is characterized by short range, low complexity, self-organization, low power consumption, and low data rate. It is mainly suitable for use in the fields of automatic control and remote control and can be embedded in various devices. ZigBee technology has powerful networking capabilities and can form star, tree and mesh networks. The appropriate network structure can be selected according to actual project needs. As shown in Figure 3, when a star topology (such as a wireless smart home system and a wireless smart agricultural monitoring system) is used, all communications are established between ordinary terminal nodes (such as smart wireless terminal devices) and a central control node (such as Between wireless intelligent gateways), the central control node is called the PAN coordinator.The central control node is the main controller of the entire ZigBee network and is also the
It is a bridge for internal network communication. It has large storage capacity and strong computing power, and can be powered by a stable power supply for a long time. Uplink and downlink data transmission can be carried out between the terminal node and the central control node. It has low cost, small storage space, weak computing power, and is powered by batteries. And the terminal nodes can only send the collected useful information to the central control node, or receive the control information sent by the central control node. If data transmission is required between terminal nodes, it must be forwarded through the central control node. [0005] It can be seen that the ZigBee network center control node and terminal nodes have typical “asymmetric” characteristics in the supply of resources (such as storage space, computing power and energy). It adopts a centralized communication control strategy, and all communications are controlled by a central node. There is two-way communication between the terminal node and the central control node. Generally, the communication link from the terminal node to the central control node is called an uplink; the communication link from the central control node to the terminal node is called a downlink.
Palavras-chave: servidor de porta série